Customize Employee Login Settings
Table of Contents
In Syncro, you set security parameters for Users on your team that are enforced whenever they log into Syncro. These employee login settings include timeouts, single sign-on parameters, and compromised password detection.
To customize employee login settings, navigate to Admin > Syncro Administration - Login Settings: 
Tip: An alternative path is via Admin > Employees - Login Settings.
Configure Timeouts
At the top of the Login Settings page, you'll see time settings for both account inactivity and MFA: 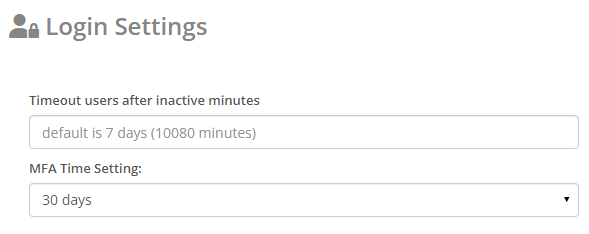
Syncro's default timeout for inactivity is 7 days (10080 minutes), you can change this by entering a new value in the “Timeout Users After Inactive Minutes” field. Be sure to enter your desired time in minutes.
The MFA Time Setting is the time between new multi-factor authentications after a User successfully authenticates from their device. The lowest you can set this to is one hour. This setting only requires a new MFA if the user signs out or closes the browser tab. If they remain logged in, go to another site, then return, Syncro will not require a new MFA.
Enable Single Sign-On
In the middle of the Login Settings page, you'll see Single Sign-On settings: 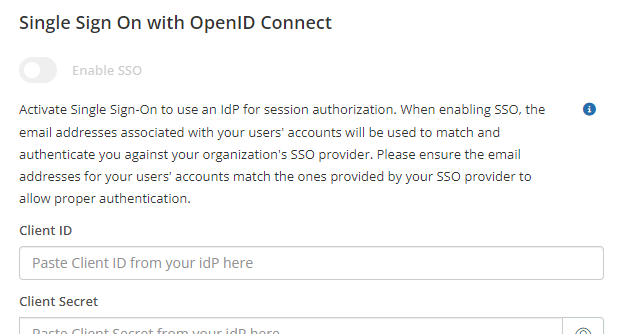
Here you can activate Single Sign-On to use an IdP for session authorization. Optionally use your Identification Provider such as Entra ID, Okta, Google Auth or more with the OpenID Connect authentication standard.
Note: When enabling SSO, the email addresses associated with your Users' accounts will be used to match and authenticate you against your organization's SSO provider. Please ensure the email addresses for your Users' accounts match the ones provided by your SSO provider to allow proper authentication.
Enable Compromised Login Password Detection
Syncro can optionally monitor whether the passwords you and your teams use to log in have previously appeared in a data breach outside of Syncro.
Note: This feature cannot be enabled if you have Single Sign-On (SSO) configured, and does not include scans of email/password combinations (i.e., it only applies to passwords).
This setting lives at the bottom of the Login Settings page:
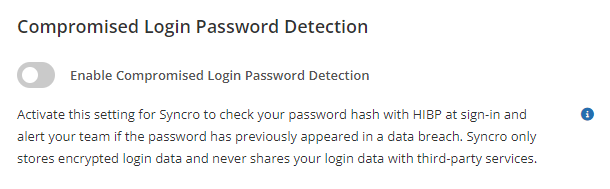
When you enable compromised login password detection, Syncro:
- Extends this monitoring setting to all users on your account,
- Securely scans your hashed password using Have I Been Pwned? (HIBP) during all future sign-ins,
- Displays an Alert in the Users table:
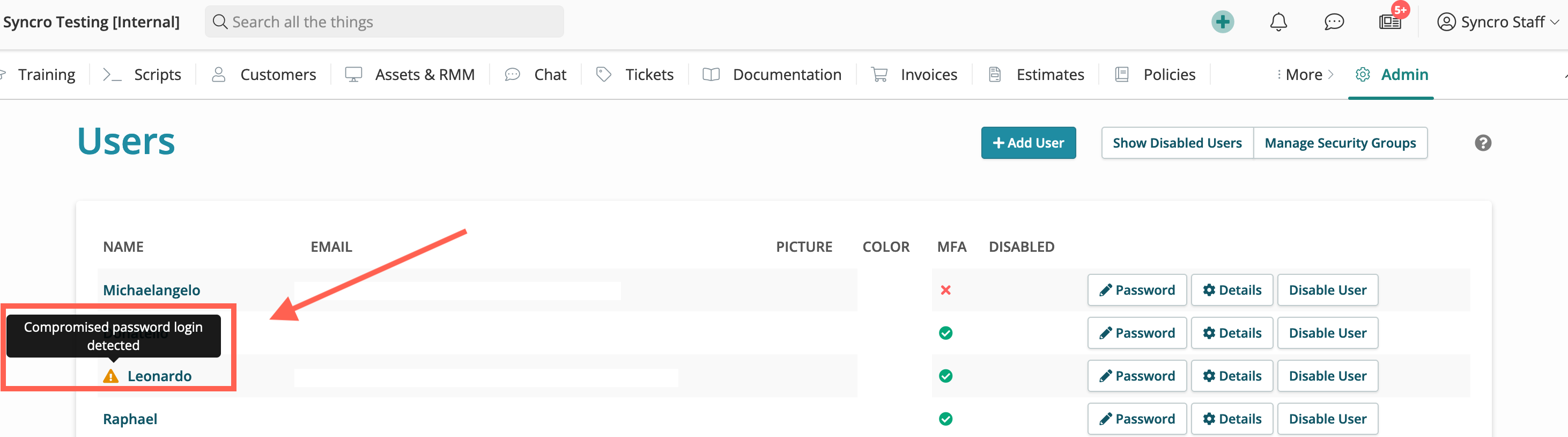
- Alerts you and your team if the password has previously appeared in a data breach, based on triggers you enable via the Notification Center:
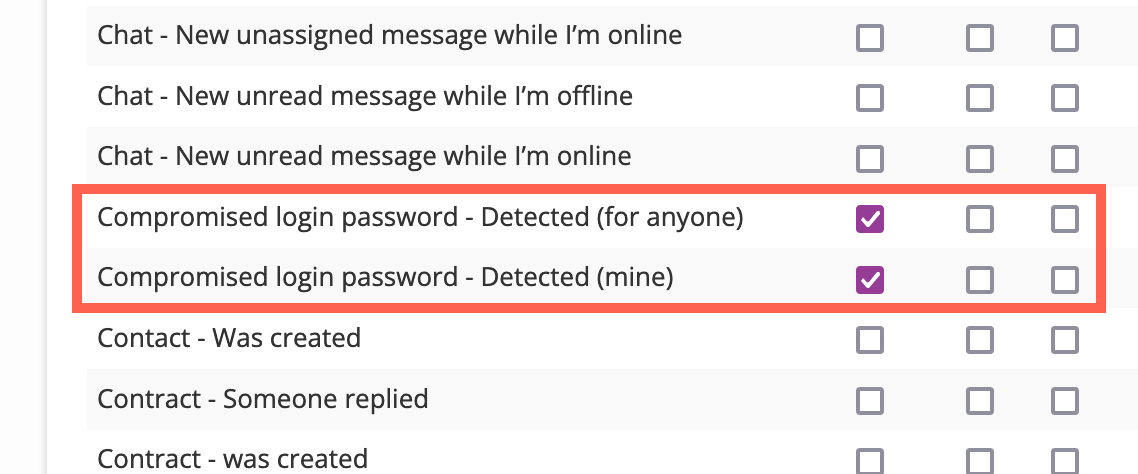
The trigger “Compromised Login Password - Detected (For Anyone)” triggers a notification when Syncro detects you or anyone else on your account has logged in with a potentially compromised password. “Compromised Login Password - Detected (Mine)” only trigger a notification when Syncro detects you—as the person currently logged into Syncro—have logged in with a potentially compromised password.
Syncro does NOT enforce that users reset passwords should they be flagged as potentially compromised. You will only be alerted to the fact so you can take action to reset these passwords anywhere they may be used. Syncro will continue to alert you with a banner after each sign-in and generate any corresponding notifications if enabled. The banner auto-dismisses after you navigate away from the page post login.
IMPORTANT: Syncro only stores encrypted login data and never shares your login data with third-party services.
